Computer Systems
Created by Commodore Wilkan Targaryen on Sat Dec 21st, 2024 @ 1:18pm
Computer Systems
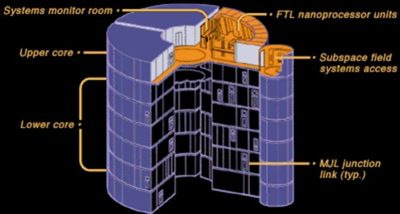 The Computer System is the most vital operational element of the Enterprise, functioning as the ship's autonomic nervous system. It is responsible for nearly every shipboard function, from life support and weapons arrays to shielding and recreational facilities. The system is so deeply integrated that a total crash would practically shut down the entire vessel. Access to these systems is strictly regulated, requiring appropriate security clearances for most high-level functions.
The Computer System is the most vital operational element of the Enterprise, functioning as the ship's autonomic nervous system. It is responsible for nearly every shipboard function, from life support and weapons arrays to shielding and recreational facilities. The system is so deeply integrated that a total crash would practically shut down the entire vessel. Access to these systems is strictly regulated, requiring appropriate security clearances for most high-level functions.The heart of this network is a set of redundant, massive cylindrical Computer Cores. The current Century Class configuration features six Computer Cores. Four of these are cutting-edge Positronic Computer Cores - with two located in the Primary Hull and two in the Engineering Hull. These cores utilize Positronic Optical Storage Chips, an advancement based on the pioneering work of Doctors Noonien and Altan Soong, Bruce Maddox, and Agnes Jurati. Two backup cores, based on older Isolinear technology, are also installed as a fail-safe. Each core stands 20 meters tall and 12 meters wide, spanning multiple decks and housing up to 200,000 chips. The primary cores in the Saucer run in parallel to provide redundancy; if one fails, the other assumes the total load instantly without interruption. Each core incorporates miniature subspace field generators that create a symmetrical field distortion, allowing the system to bridge the subspace boundary layer, enabling faster-than-light (FTL) data processing and transmission that far exceeds standard optical speeds.
The Computer Cores are linked to the ship's Optical Data Network (ODN) via Micron Junction Links (MJL) and is augmented by a network of optical subprocessors distributed throughout the ship. While these subprocessors do not utilize FTL elements, they improve response times by distributing the computational load. Every console, replicator, and sensor is connected to this network, with control panels being pinged by LCARS every 30 milliseconds to ensure real-time responsiveness. Dedicated subprocessors and protected optical conduits are assigned to the Main Bridge and Combat Information Center to maintain control even during primary network failures. For further redundancy, the ship utilizes short-range radio frequency (RF) links to communicate with handheld devices like tricorders and PADDs, and in grave situations, these RF links can serve as an emergency data network for the entire ship.
Crew interaction is facilitated by the Library Computer Access and Retrieval System (LCARS). This software provides a seamless graphic and verbal interface, allowing the crew to monitor systems and access nearly unlimited data. Modern LCARS is integrated with the Artificial Intelligence Monitoring Software (AIMS), a highly sophisticated subroutine that approaches true sentience. AIMS monitors all shipboard activity and crew status via communicator badge data. In emergencies, AIMS can assess threats, notify relevant personnel, and even operate the ship based on the crew's last instructions. To prevent data loss, AIMS maintains a continuous backup of mission parameters, allowing the system to recover from a complete data purge by reverting to its most recent stable configuration. In the event that the ship goes without commands from the crew for longer than 10 days, AIMS has an internal recall function and will automatically pilot the ship back to the home base at maximum safe speed.
Artificial Intelligence Monitoring Software (AIMS)
 The Artificial Intelligence Monitoring Software (AIMS) represents the current apex of sentient programming and software engineering. An outgrowth of the EXEO Holographic Core and Emergency Command Hologram (ECH) architectures, AIMS utilizes multiple parallel processors and quantum computing to facilitate billions of concurrent tasks. While historical AI systems struggled to match the nuance of the humanoid brain, AIMS achieves comparable sophistication thanks to the Postronic Matrix, allowing it to reason independently, form new conclusions, and alter its responses based on experiential data.
The Artificial Intelligence Monitoring Software (AIMS) represents the current apex of sentient programming and software engineering. An outgrowth of the EXEO Holographic Core and Emergency Command Hologram (ECH) architectures, AIMS utilizes multiple parallel processors and quantum computing to facilitate billions of concurrent tasks. While historical AI systems struggled to match the nuance of the humanoid brain, AIMS achieves comparable sophistication thanks to the Postronic Matrix, allowing it to reason independently, form new conclusions, and alter its responses based on experiential data.The system is instrumental in nearly all aspects of starship operations, from organizing internal traffic to performing specialized tasks such as mapping entire solar systems or calculating the trajectories of every asteroid in a high-density belt. In combat, AIMS has revolutionized warfare by processing sensor signatures (such as identifying the launch point, timing, and type of an incoming missile) and initiating counter-salvos faster than any organic operator. In high-risk scenarios, AIMS serves as a vital failsafe. Inspired by the ECH concept first implemented on the USS Voyager, AIMS can act as a "backup captain." Upon the transfer of command codes via verbal authorization, the AI possesses acting command authority, with access to all Starfleet strategic and tactical databases. It can manually or digitally interact with ship systems, perform engineering assessments, and even execute critical emergency procedures like the ejection of the warp core.
The AI can be configured in two distinct operational states:
- Read-Only Mode: The default setting for routine operations. The system operates within the literal interpretation of mission parameters, acting as a highly efficient tool following direct orders.
- Read/Write Mode: In this state, Adaptive Learning Software is activated, allowing the AI to self-initiate tasks and develop a unique personality. This mode permits introspective analysis, enabling the AI to better adapt to novel situations outside standard efficiency requirements.
Library Computer Access and Retrieval System (LCARS)
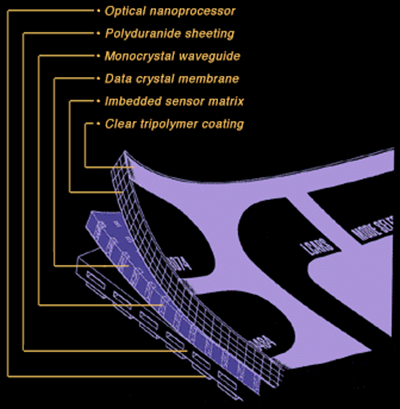 The Library Computer Access and Retrieval System (LCARS) is an exceptionally flexible suite of software routines that governs the operation of all computerized systems aboard Starfleet vessels and facilities. Deployed in the mid-24th century to replace the Spacecraft Operating and Management System (S/COMS) of the previous era, LCARS serves as the primary interface between the crew and the ship’s central computer cores. By using sophisticated subroutines to process instructions, LCARS allows the execution of complex tasks through only a few commands, facilitating the retrieval and storage of massive databases.
The Library Computer Access and Retrieval System (LCARS) is an exceptionally flexible suite of software routines that governs the operation of all computerized systems aboard Starfleet vessels and facilities. Deployed in the mid-24th century to replace the Spacecraft Operating and Management System (S/COMS) of the previous era, LCARS serves as the primary interface between the crew and the ship’s central computer cores. By using sophisticated subroutines to process instructions, LCARS allows the execution of complex tasks through only a few commands, facilitating the retrieval and storage of massive databases.LCARS can be accessed from virtually anywhere on the ship through either voice or keyboard commands. While the system incorporates sophisticated algorithms, most personnel prefer the keyboard interface for its greater operating speed and reduced error rate. The physical construction of an LCARS display panel is a marvel of material science and is remarkably resilient. Composed of three primary layers, the substrate contains optical nanoprocessors that allow the panel to be self-configuring and include nonvolatile memory to ensure function even without main computer support. The display membrane is a high-resolution monitor supporting the graphical interface. Finally, the outer layer is constructed of transparent aluminum and contains a sensor matrix to detect tactile input and a matrix providing auditory and tactile feedback. While Starfleet still favors using two-dimensional touch interfaces, LCARS can also generate three-dimensional holographic interfaces.
Each interface maintains a logical organizational flow and intuitive grouping of functions, with its software-defined surface tied into a local subprocessor. This subprocessor monitors operator habits and compares them to predefined scenarios, allowing the interface to anticipate demands and reconfigure itself to present the most frequently chosen courses of action. The display surfaces are extremely customizable, allowing crewmembers to store personal preferences; in the event of a system upgrade, the interface can even be instructed to emulate older software versions until the user is properly trained.
Optical Data Network
 The Optical Data Network (ODN) is the sophisticated neurological system of the Enterprise, functioning as a complex collection of multiplexed optical monocrystal microfibers that facilitate data transmission across the entire vessel. The fundamental operation of the ODN relies on converting electrical signals into pulses of light, which are then transmitted through thin strands of crystal fiber to a photodetector processor. This destination processor converts the light pulses back into electrical signals for use by shipboard systems. Because light possesses an extremely high frequency and experiences minimal signal degradation, the ODN can support massive data flows and near-instantaneous transmission speeds over long distances.
The Optical Data Network (ODN) is the sophisticated neurological system of the Enterprise, functioning as a complex collection of multiplexed optical monocrystal microfibers that facilitate data transmission across the entire vessel. The fundamental operation of the ODN relies on converting electrical signals into pulses of light, which are then transmitted through thin strands of crystal fiber to a photodetector processor. This destination processor converts the light pulses back into electrical signals for use by shipboard systems. Because light possesses an extremely high frequency and experiences minimal signal degradation, the ODN can support massive data flows and near-instantaneous transmission speeds over long distances.To ensure total system stability, the network is anchored by a series of five redundant major optical trunks that link the primary computer cores in the Saucer Section with those located in the Stardrive. This architecture is designed for extreme resilience with any single major trunk capable of handling the entire data load of the ship’s basic operating systems. These trunks also provide critical information links to optical subprocessors distributed throughout the spacecraft. These subprocessors increase system efficiency by distributing the computational load and providing localized redundancy in the event of a major system failure.
The distribution of data continues from these subprocessors via secondary ODN links that connect to every individual control panel, terminal, and display surface on the ship. Beyond the primary infrastructure, the vessel incorporates two secondary optical data networks specifically designed to provide protected linkages to mission-critical systems and stations. To prevent a single localized event from disabling all communications, these backup networks are physically separated from the primary system and from each other. An inherent advantage of this fiber-optic design is its immunity to electromagnetic interference, ensuring that the connection between the central Computer Cores and the ship’s various subprocessors remains stable and reliable even during intense combat or when encountering spatial anomalies.
Optical Storage Chip
An Optical Storage Chip is an advanced electronic component that uses light to store and retrieve digital data.
Isolinear Optical Storage Chip
 In the late 24th century, Isolinear Optical Chips were the standard information storage and software medium used by Starfleet. With the emergence of Positronic Optical Storage Chips, these devices have taken on a secondary role within Federation computer systems. Each chip utilizes single-axis optical crystal layering to achieve subwavelength switching distances, providing a total memory capacity of 2.15 kiloquads in standard holographic format. A critical feature of the isolinear architecture is the integration of onboard nanoprocessors that manage data configuration and retrieval independently of the Library Computer Access and Retrieval System (LCARS).
In the late 24th century, Isolinear Optical Chips were the standard information storage and software medium used by Starfleet. With the emergence of Positronic Optical Storage Chips, these devices have taken on a secondary role within Federation computer systems. Each chip utilizes single-axis optical crystal layering to achieve subwavelength switching distances, providing a total memory capacity of 2.15 kiloquads in standard holographic format. A critical feature of the isolinear architecture is the integration of onboard nanoprocessors that manage data configuration and retrieval independently of the Library Computer Access and Retrieval System (LCARS).Superconductive, Isolinear Chips are installed within a Backup Computer Core and are designed to interface seamlessly with other architectures, specifically the Positronic Chips used elsewhere on the ship. Entire banks of Isolinear Chips and independent subprocessors are linked via the ship's Optical Data Network (ODN) with the Positronic Cores to share computational loads. While Isolinear Chips lack fuzzy logic capabilities, their massive computational abilities and portability still make them efficient options for storing enormous datasets.
Beyond the controlled environment of a Computer Core, Isolinear Chips are highly versatile due to specific ruggedization techniques and are still used in many technologies even in the 25th Century, often serving as the primary form of information transport for handheld devices. Isolinear Chips are resilient enough to be handled without protective gloves and are shielded against corruption in hostile environments. This robust design ensures that even if a ship is severely damaged, its flight records and medical scans remain accessible. Whether supporting the complex library trade or enabling the daily functions of an infirmary, the Isolinear Optical Chip remains a reliable and ubiquitous storage technology in the Federation.
Positronic Optical Storage Chip
 The most sophisticated computational architecture currently utilized by Starfleet, the Computer Cores of the Century-class incorporate Positronic Optical Storage Chips as their default storage medium. This technology facilitates an artificial neural network designed to achieve sentience by imitating the complex architecture of the humanoid brain. While originally conceptualized by 20th-century author Isaac Asimov and perfected by Dr. Noonien Soong, the modern stable positronic net was finalized by the Daystrom Institute in the early 25th Century. These systems function as "learning computers," utilizing a "hypercube" physical connection scheme. This lattice of cubes minimizes effective communication distances between processors, allowing the hardware to adapt and build new logical connection schemes even when the software's requirements cannot be predicted in advance.
The most sophisticated computational architecture currently utilized by Starfleet, the Computer Cores of the Century-class incorporate Positronic Optical Storage Chips as their default storage medium. This technology facilitates an artificial neural network designed to achieve sentience by imitating the complex architecture of the humanoid brain. While originally conceptualized by 20th-century author Isaac Asimov and perfected by Dr. Noonien Soong, the modern stable positronic net was finalized by the Daystrom Institute in the early 25th Century. These systems function as "learning computers," utilizing a "hypercube" physical connection scheme. This lattice of cubes minimizes effective communication distances between processors, allowing the hardware to adapt and build new logical connection schemes even when the software's requirements cannot be predicted in advance.The standard linear computational speed for a positronic subprocessor is rated at 60 trillion operations per second, with an ultimate storage capacity of 100 petabytes. This performance is achieved through the use of Quantum Effects (QE) chips, which move beyond binary systems into a realm where quadrillions of simultaneous switching positions occur at each quantum level. These processes take place near the Planck length, utilizing 10-dimensional building blocks significantly smaller than a single proton. When integrated into a starship core, an asynchronous interlink sequencer removes the performance constraints typically created by physical gaps between positronic links, resulting in virtually instantaneous computational speeds.
Structurally, the finished CPU exists as a thick, three-dimensional circuit board approximately 35 mm in diameter, housed within inertial shock dampers to protect the "soul" of the unit. The design mirrors evolutionary biology, featuring a massively parallel system of processor blocks connected by high-capacity "data pipes" for both local and long-range communication. Unlike isolinear chips that rely on exhaustive calculations, these positronic systems utilize fuzzy logic. This enables the computer to effectively "think" like a living organism, employing "best-guess" decision-making to resolve complex problems. Depending on mission parameters, these units can be set to "read-only" presets to restrict adaptation to specific mission needs or granted full autonomy to independently learn and adapt.
Despite their high performance, the positronic network is susceptible to environmental and energy-based interference. Ionic interference can scramble circuits, while plasma shocks may cause file directories to inaccurately exchange data. The system also remains at risk of cascade anomalies, which are structural instabilities that can render the network non-functional. Resonance effects from Dekyon field emissions can occur within the subprocessors, potentially transmitting information through temporal instabilities. Furthermore, the source code remains vulnerable to malicious alteration via a Positronic Decompiler, which can change the core behavior of the intelligence.
The operational characteristics of these systems are often determined by the phase discriminator. Production model Century-class vessels typically employ the standard "Type R" discriminator, whereas first-generation vessels, including the Enterprise, utilize the more aggressive and occasionally unstable "Type L" variant. While the long-term effects of space travel on these neural nets are under ongoing study, the subprocessors maintain high versatility, capable of emitting high-frequency interphasic pulses to neutralize external threats such as interphasic organisms.
Navigational Computer and Database Management
 To ensure the operational safety of the Starship Enterprise, a dedicated Navigational Computer System is utilized to assist Flight Control (Conn) and Astrometric functions. While earlier starship generations processed navigation as a subsystem of the main computer, the advent of high-velocity propulsion (including Coaxial Warp and Quantum Slipstream) necessitated dedicated hardware. This system processes massive data streams from long-range, lateral, and specialized navigational sensors to pinpoint the vessel's location.
To ensure the operational safety of the Starship Enterprise, a dedicated Navigational Computer System is utilized to assist Flight Control (Conn) and Astrometric functions. While earlier starship generations processed navigation as a subsystem of the main computer, the advent of high-velocity propulsion (including Coaxial Warp and Quantum Slipstream) necessitated dedicated hardware. This system processes massive data streams from long-range, lateral, and specialized navigational sensors to pinpoint the vessel's location.Accuracy is paramount; the system can determine its position relative to the galactic center or Earth to within 10 kilometers at sublight speeds and within 100 kilometers during faster-than-light travel. For precision maneuvers, such as docking, the system maintains a tolerance of 2.00 centimeters. This precision is supported by the Galactic Condition Database, a massive map of the galaxy synthesized from subspace relays, probes, and Starfleet telescopes. Because the galaxy is in constant motion and subject to observational time lags, the computer employs complex algorithms and predictive language to estimate the movement of stellar phenomena to aid in navigation.
Velocity calculations are further refined by the Federation Timebase Beacon network, which provides absolute time values. During travel where beacon contact is lost, onboard processors maintain records, though these are subject to temporal distortion—particularly at high impulse speeds. The navigational computer automatically compensates for these distortions and synchronizes with the network upon the next available handshake.
Guidance, Orientation, and Autopilot Functions
Guidance is governed by the computer's ability to interpret commands from the Commanding Officer and develop optimal flight paths. It constantly monitors for hazards such as stars, nebulae, or subspace phenomena. In the event of a flight path risk, the computer can independently remedy the situation via course alteration or the Main Deflector, or provide a list of resolutions to the Flight Controller.The system is supported by two critical sub-functions:
- Attitude Control: This system maintains the ship’s orientation along its projected path. Distinct from inertial damping, Attitude Control prevents uncontrolled wobbling, shaking, or yawing, ensuring the ship remains stable enough for precise steering.
- Autopilot: Managed by the Navigational Computer and Artificial Intelligence Monitoring Software, this function maintains flight operations when the pilot is incapacitated or otherwise unable to manually control the vessel.
Navigational Input and Vectoring
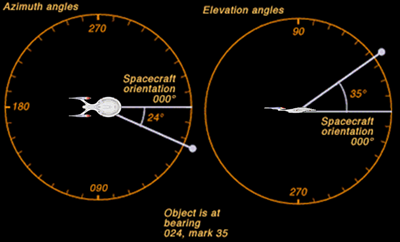 The Flight Controller (or Helmsman) executes navigational orders using five primary methods of input. These vectors are typically translated into two perpendicular planes to define the ship's trajectory:
The Flight Controller (or Helmsman) executes navigational orders using five primary methods of input. These vectors are typically translated into two perpendicular planes to define the ship's trajectory:
- Destination Name (Planet, System, or Facility): This is the most common method of navigation. The operator designates a specific celestial object or orbital facility stored within the navigational database, and the computer automatically plots the optimal trajectory.
- Sector Designation: If a broader destination is required, the computer can plot a course to the geometric center of a specific sector, identified by its name or ID number.
- Spacecraft Interception: For moving targets identified by the ship's sensors, the computer plots a relative intercept course. This requires the operator to input either a specific velocity or a desired interception time so the computer can calculate the meeting point relative to the other craft's position.
- Relative Bearing: This method describes a flight vector based on the ship's current orientation. It utilizes two 360-degree planes: a horizontal plane (increasing to starboard) and a vertical plane (increasing above the ship). For example, a heading of 000 mark 0 indicates straight ahead, while 150 mark 20 indicates a turn 150 degrees to starboard with a 20-degree upward pitch.
- Absolute Heading: Primarily used for galactic-scale navigation, this process involves specifying an azimuth and elevation relative to the galactic center. A heading of 000 mark 0 represents a direct course toward the galactic core, serving as a universal reference point similar to a planetary north pole.
During transit, the computer constantly updates these flight plans, integrating real-time sensor data and logs from other Federation vessels to adjust for the dynamic nature of the interstellar environment.
Threat Assessment/Tracking/Targeting System
 The Threat Assessment/Tracking/Targeting System (TA/T/TS), frequently referred to in operational contexts as "Targeting Scanners," represents the integration of a starship's Tactical Computer and Tactical Sensor Arrays into a unified offensive and defensive package. While most Federation vessels utilize a TA/T/TS module built directly into the bridge tactical console, the Enterprise employs a significantly more robust architecture integrated into the Main Computer Core. This centralized integration provides the system with superior processing power, allowing it to provide a persistent, high-fidelity review of all incoming data to identify potential threats to the vessel’s safety.
The Threat Assessment/Tracking/Targeting System (TA/T/TS), frequently referred to in operational contexts as "Targeting Scanners," represents the integration of a starship's Tactical Computer and Tactical Sensor Arrays into a unified offensive and defensive package. While most Federation vessels utilize a TA/T/TS module built directly into the bridge tactical console, the Enterprise employs a significantly more robust architecture integrated into the Main Computer Core. This centralized integration provides the system with superior processing power, allowing it to provide a persistent, high-fidelity review of all incoming data to identify potential threats to the vessel’s safety.During tactical engagements, the TA/T/TS optimizes shipboard efficiency by coordinating combat maneuvers with weapon deployment. The system performs a comprehensive structural and defensive analysis of any detected opponent to identify vulnerable systems or hull weak points, subsequently recommending optimal targeting solutions to the Tactical Officer. For high-intensity scenarios, the system can be configured for automated threat targeting, allowing for near-instantaneous response times against incoming projectiles or multiple hostile vessels. TA/T/TS is a cornerstone of the Enterprise's Point Defense Phaser System, which destroys incoming weapons before they can do any damage.
Given its status as a high-priority target during hostilities, the TA/T/TS is designed with extreme resilience. The system incorporates redundant backups within the computer core, ensuring that backup processors can be brought online within seconds should the primary system suffer a failure or battle damage. Beyond its primary role in weapons governance and shield modulation, the Targeting Scanners serve a critical function for the transporter rooms. The high-resolution tracking data provided by the TA/T/TS is the primary source used to establish and maintain a Transporter Lock on moving or distant targets, ensuring personnel and cargo safety during beam-out procedures.
Anti-Intruder System
Tied closely to the Internal Security Sensors, the Anti-Intruder System (AIS) is a high-level subsystem of the Threat Assessment/Tracking/Targeting System (TA/T/TS). It is specifically engineered to identify and incapacitate hostile forces that have breached the vessel's hull. Using information from the Anti-Intruder System, Security teams can be deployed and directed via voice command or keyed instructions by the Security Officer or an authorized deputy.The primary operational protocol for the AIS involves the deployment of localized containment fields, designed to trap an intruder within a specific corridor or compartment until a Security Team can be dispatched for apprehension. In scenarios where an intruder attempts to compromise the ship's Computer Systems, the AIS can escalate its response by deploying a mild electric shock. This discharge is calibrated to a strength equivalent to a Level 1 Phaser setting, sufficient to incapacitate the target and prevent unauthorized system access without necessitating lethal force.
Command Authorization and Security Clearance
 Starfleet personnel assigned to Federation vessels are governed by a tiered access hierarchy managed by the Threat Assessment/Tracking/Targeting System. This structure ensures that command functions and sensitive data remain restricted to authorized personnel based on rank, role, and operational necessity.
Starfleet personnel assigned to Federation vessels are governed by a tiered access hierarchy managed by the Threat Assessment/Tracking/Targeting System. This structure ensures that command functions and sensitive data remain restricted to authorized personnel based on rank, role, and operational necessity.Standard access is granted through an Authorization Code, an alphanumeric sequence consisting of the user’s last name, Greek letters, and a numerical string. These codes are typically entered via voice command, though manual keypad entry remains a secondary option. All entries require biometric confirmation by the vessel's computer system.
While the system default requires manual password entry for every instance of sensitive data access, the Artificial Intelligence Monitoring Software can be configured for persistent recognition based on an individual’s biometric profile. To mitigate risks of sabotage or security breaches, all authorization codes must be rotated every 90 days as a matter of standard security policy.
Command Authorization dictates the degree of control a user exerts over shipboard systems and high-level decision-making. The highest tier of authority, held exclusively by the Commanding Officer (CO) and Executive Officer (XO), is Alpha-Two Clearance. While both officers share this clearance level, the Captain’s orders possess absolute priority, overriding all other shipboard commands. Only an Admiral’s directives can supersede the Captain’s authority. The Senior Staff possess elevated access privileges, but they are restricted from localizing primary command functions, a security measure designed to maintain a centralized chain of command.
Distinct from Command Authorization, Security Clearance is the specific level of data access granted to a crewmember. This is determined by a combination of rank, professional status, and specific departmental position. This clearance acts as the primary filter for accessing sensitive computer databases or executing specialized technical tasks. Clearance levels are dynamic; they can be upgraded, transferred to other officers, or terminated instantly. This administrative control is restricted to the Commanding Officer, Executive Officer, Chief Operations Officer, and the Chief Security Officer.
Security Clearance | ||||
| Commanding Officer | All Flag Ranks Captain (Enterprise) |
Alpha Two | 10 | User has unlimited access to all command functions, computer records, and shipboard systems, including the ability to localize command functions. |
| Executive Officer | Captain | Alpha Two | 09 | User has unlimited access to all command functions, computer records, and shipboard systems, including limited ability to localize command functions. |
| Second Officer Chief Engineering Officer Chief Operations Officer |
Commander | Alpha One | 08 | User has unlimited access to all command functions, computer records, and shipboard systems, but no ability to localize command functions. |
| Chief Flight Control Officer Chief Medical Officer Chief Science Officer Chief Security/Tactical Officer Assistant Chief Engineering Officer Assistant Chief Operations Officer |
Lieutenant Commander | Beta Two | 07 | User has unlimited access to all computer records and shipboard systems, but limited access to command functions. |
Assistant Chief Flight Control Officer Assistant Chief Medical Officer Assistant Chief Science Officer Assistant Chief Security/Tactical Officer Engineering Officer Operations Officer Medical Officer/Counselor |
Lieutenant Master Chief Petty Officer |
Beta One | 06 | User has unlimited access to all computer records, but limited access to command functions and systems related to their duties. |
| Flight Control Officer Medical Officer Science Officer Security/Tactical Officer Engineering Specialist Transporter Specialist |
Lieutenant (Junior Grade) Chief Warrant Officer Senior Chief Petty Officer |
Gamma Two | 05 | User has limited access to command functions, computer records, and shipboard systems related to their duties. |
| Nurse Pilot Science Specialist Yeoman |
Ensign Master Warrant Officer Chief Petty Officer |
Gamma One | 04 | User has limited access to computer records and shipboard systems related to their duties, but no access to command functions. |
| Civilian Consultants | Staff Warant Officer Petty Officer 1st, 2nd, and 3rd Class | Delta Two | 03 | User has limited access to computer records and monitored access to shipboard systems, but no access to command functions or shipboard systems. |
| Cadet Warrant Officer Crewman Recruit Crewman Apprentice Crewman Civilian Personnel |
Delta One | 02 | User has limited, monitored access to computer records related to their duties, but no access to command functions or shipboard systems. | |
| 01 | User has access to open records only with no access to command functions, computer records, or shipboard systems. | |||
Transponder Systems and Prefix Code Protocols
 To maintain the security and tactical integrity of its fleet, Starfleet utilizes a dual-layered system of identification and remote command override managed by the Threat Assessment/Tracking/Targeting System. The first layer consists of Transponder Codes, which act as an Identification: Friend or Foe (IFF) signal with origins dating back to 20th-century terrestrial aircraft. These codes transmit essential data including a vessel's name, class, and political allegiance via subspace. Because transponder signals can be detected over vast distances, they allow fleet commanders to coordinate ship deployments far beyond the effective range of standard sensors. Federation starships automatically cross-reference these signals with onboard databases and Warp signature profiles to gain a comprehensive tactical picture of approaching vessels. Transponder signals are also vital for search and rescue operations. In the event of a catastrophic hull failure, a ship's flight recorder will continue to transmit a transponder signal to facilitate location and retrieval, even if the vessel's primary energy signatures have been neutralized.
To maintain the security and tactical integrity of its fleet, Starfleet utilizes a dual-layered system of identification and remote command override managed by the Threat Assessment/Tracking/Targeting System. The first layer consists of Transponder Codes, which act as an Identification: Friend or Foe (IFF) signal with origins dating back to 20th-century terrestrial aircraft. These codes transmit essential data including a vessel's name, class, and political allegiance via subspace. Because transponder signals can be detected over vast distances, they allow fleet commanders to coordinate ship deployments far beyond the effective range of standard sensors. Federation starships automatically cross-reference these signals with onboard databases and Warp signature profiles to gain a comprehensive tactical picture of approaching vessels. Transponder signals are also vital for search and rescue operations. In the event of a catastrophic hull failure, a ship's flight recorder will continue to transmit a transponder signal to facilitate location and retrieval, even if the vessel's primary energy signatures have been neutralized.The second and more critical layer of security is the Prefix Code. Originally developed in the early 23rd century following an operational order from Starfleet Security, the Prefix Code is a classified alphanumeric sequence inserted into the fundamental operational coding of every shipboard system. Every Starfleet vessel is assigned a unique code upon launch, and a master record of these codes is maintained by all other Federation ships for use in extreme emergencies. This defensive protocol is designed to prevent unauthorized personnel from seizing control of a ship's computer and to allow authorized Starfleet personnel to remotely override the command functions of a vessel that has been hijacked by hostile forces.
Due to their sensitivity, access to Prefix Codes is strictly limited to personnel with Level 10 Clearance, typically the Commanding Officer and Starfleet Command. When utilized from another starship, the commanding vessel transmits a background data packet containing the specific code via subspace. Once authenticated, the user gains direct control over the target vessel's engines, weapons, and defenses, effectively bypassing bridge controls and lowering shields. Starfleet Command routinely monitors these codes to prevent sabotage. If an attempt is made to modify a Prefix Code while the vessel is within subspace range of Starfleet, the main computer initiates a return protocol and notifies Starfleet Security of its location. Furthermore, Starfleet officers maintain personal command codes for remote access, which are immediately altered if an officer is captured. In tactical scenarios where a captain has been seized, the submission of a compromised prefix code can be used to alert the fleet to the location of the attempted infiltration and the presence of the captured officer.
Categories: Command | Tactical | Personnel | Operations | Science